An understanding of privacy, security, or consent of PHI among employees
XYZ Medical Center
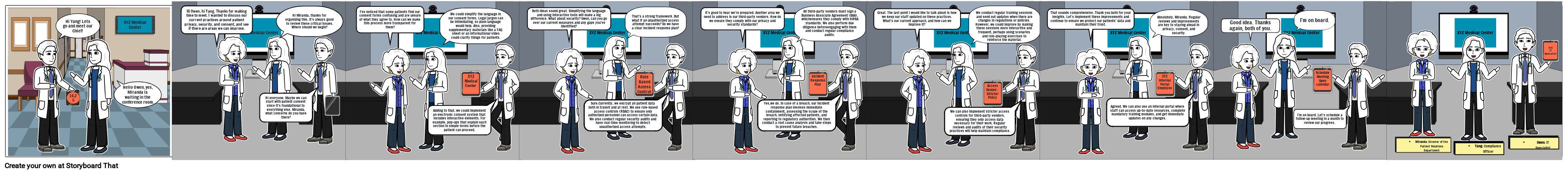
Hi Yang! Lets go and meet our Chief!
Hello Owen, yes, Miranda is waiting in the conference room.
XYZ Medical Center
Hi Owen, hi Yang. Thanks for making time to meet. I wanted to discuss our current practices around patient privacy, security, and consent, and see if there are areas we can improve.
Hi Miranda, thanks for organizing this. It’s always good to review these critical issues. Where should we begin?
Hi everyone. Maybe we can start with patient consent since it’s foundational to everything else. Miranda, what concerns do you have there?
XYZ Medical Center
I've noticed that some patients find our consent forms confusing and are unsure of what they agree to. How can we make this process more transparent for them?
We could simplify the language in our consent forms. Legal jargon can be intimidating, so plain language would help. Also, providing supplementary materials like a FAQ sheet or an informational video could clarify things for patients.
Adding to that, we could implement an electronic consent system that includes interactive elements. For example, pop-ups that explain each section in simple terms before the patient can proceed.
14:25
XYZ
Medical Center
XYZ Medical Center
Both ideas sound great. Simplifying the language and using interactive tools will make a big difference. What about security? Owen, can you go over our current measures and any gaps you’ve identified?
That’s a strong framework. But what if an unauthorized access attempt succeeds? Do we have a clear incident response plan?
Sure.Currently, we encrypt all patient data both in transit and at rest. We use role-based access controls (RBAC) to ensure only authorized personnel can access certain data. We also conduct regular security audits and have real-time monitoring to detect unauthorized access attempts.
Role Based
Access
Control
XYZ Medical Center
It’s good to hear we’re prepared. Another area we need to address is our third-party vendors. How do we ensure they comply with our privacy and security standards?
All third-party vendors must sign a Business Associate Agreement (BAA), whichensures they comply with HIPAA standards. We also perform due diligence beforeengaging with them and conduct regular compliance audits.
Yes,we do. In case of a breach, our incident response plan involves immediate containment, assessing the scope of the breach, notifying affected patients, and reporting to regulatory authorities. We then conduct a root cause analysis and take steps to prevent future breaches.
Incident Response Plan
XYZ Medical Center
Great. The last point I would like to talk about is how we keep our staff updated on these practices. What’s our current approach, and how can we improve it?
We conduct regular training sessions and send out updates when there are changes in regulations or policies. However, we could improve by making these sessions more interactive and frequent, perhaps using scenarios and role-playing exercises to reinforce the material.
We can also implement stricter access controls for third-party vendors, ensuring they only access data necessary for their work. Regular reviews and audits of their security practices will help maintain compliance.
Access Denied - Stricter Policy
XYZ Medical Center
That sounds comprehensive. Thank you both for your insights. Let’s implement these improvements and continue to ensure we protect our patients’ data and maintain their trust.
Absolutely, Miranda. Regular reviews and improvements are key to staying ahead in privacy, consent, and security.
Agreed. We can also use an internal portal where staff can access up-to-date resources, complete mandatory training modules, and get immediate updates on any changes.
XYZ Internal Portal Employee
XYZ Medical Center
Good idea. Thanks again, both of you.
I’m on board.
I’m on board. Let’s schedule a follow-up meeting in a month to review our progress.
Schedule Meeting Open calendar
XYZ Medical Center
- Miranda: Director of the Patient Relations Department
- Yang: Compliance Officer
- Owen: IT Specialist
XYZ
IT Specialist
XYZ Medical Center
Hi Yang! Lets go and meet our Chief!
Hello Owen, yes, Miranda is waiting in the conference room.
XYZ Medical Center
Hi Owen, hi Yang. Thanks for making time to meet. I wanted to discuss our current practices around patient privacy, security, and consent, and see if there are areas we can improve.
Hi Miranda, thanks for organizing this. It’s always good to review these critical issues. Where should we begin?
Hi everyone. Maybe we can start with patient consent since it’s foundational to everything else. Miranda, what concerns do you have there?
XYZ Medical Center
I've noticed that some patients find our consent forms confusing and are unsure of what they agree to. How can we make this process more transparent for them?
We could simplify the language in our consent forms. Legal jargon can be intimidating, so plain language would help. Also, providing supplementary materials like a FAQ sheet or an informational video could clarify things for patients.
Adding to that, we could implement an electronic consent system that includes interactive elements. For example, pop-ups that explain each section in simple terms before the patient can proceed.
14:25
XYZ
Medical Center
XYZ Medical Center
Both ideas sound great. Simplifying the language and using interactive tools will make a big difference. What about security? Owen, can you go over our current measures and any gaps you’ve identified?
That’s a strong framework. But what if an unauthorized access attempt succeeds? Do we have a clear incident response plan?
Sure.Currently, we encrypt all patient data both in transit and at rest. We use role-based access controls (RBAC) to ensure only authorized personnel can access certain data. We also conduct regular security audits and have real-time monitoring to detect unauthorized access attempts.
Role Based
Access
Control
XYZ Medical Center
It’s good to hear we’re prepared. Another area we need to address is our third-party vendors. How do we ensure they comply with our privacy and security standards?
All third-party vendors must sign a Business Associate Agreement (BAA), whichensures they comply with HIPAA standards. We also perform due diligence beforeengaging with them and conduct regular compliance audits.
Yes,we do. In case of a breach, our incident response plan involves immediate containment, assessing the scope of the breach, notifying affected patients, and reporting to regulatory authorities. We then conduct a root cause analysis and take steps to prevent future breaches.
Incident Response Plan
XYZ Medical Center
Great. The last point I would like to talk about is how we keep our staff updated on these practices. What’s our current approach, and how can we improve it?
We conduct regular training sessions and send out updates when there are changes in regulations or policies. However, we could improve by making these sessions more interactive and frequent, perhaps using scenarios and role-playing exercises to reinforce the material.
We can also implement stricter access controls for third-party vendors, ensuring they only access data necessary for their work. Regular reviews and audits of their security practices will help maintain compliance.
Access Denied - Stricter Policy
XYZ Medical Center
That sounds comprehensive. Thank you both for your insights. Let’s implement these improvements and continue to ensure we protect our patients’ data and maintain their trust.
Absolutely, Miranda. Regular reviews and improvements are key to staying ahead in privacy, consent, and security.
Agreed. We can also use an internal portal where staff can access up-to-date resources, complete mandatory training modules, and get immediate updates on any changes.
XYZ Internal Portal Employee
XYZ Medical Center
Good idea. Thanks again, both of you.
I’m on board.
I’m on board. Let’s schedule a follow-up meeting in a month to review our progress.
Schedule Meeting Open calendar
XYZ Medical Center
- Miranda: Director of the Patient Relations Department
- Yang: Compliance Officer
- Owen: IT Specialist
XYZ
IT Specialist
XYZ Medical Center
Hi Yang! Lets go and meet our Chief!
Hello Owen, yes, Miranda is waiting in the conference room.
XYZ Medical Center
Hi Owen, hi Yang. Thanks for making time to meet. I wanted to discuss our current practices around patient privacy, security, and consent, and see if there are areas we can improve.
Hi Miranda, thanks for organizing this. It’s always good to review these critical issues. Where should we begin?
Hi everyone. Maybe we can start with patient consent since it’s foundational to everything else. Miranda, what concerns do you have there?
XYZ Medical Center
I've noticed that some patients find our consent forms confusing and are unsure of what they agree to. How can we make this process more transparent for them?
We could simplify the language in our consent forms. Legal jargon can be intimidating, so plain language would help. Also, providing supplementary materials like a FAQ sheet or an informational video could clarify things for patients.
Adding to that, we could implement an electronic consent system that includes interactive elements. For example, pop-ups that explain each section in simple terms before the patient can proceed.
14:25
XYZ
Medical Center
XYZ Medical Center
Both ideas sound great. Simplifying the language and using interactive tools will make a big difference. What about security? Owen, can you go over our current measures and any gaps you’ve identified?
That’s a strong framework. But what if an unauthorized access attempt succeeds? Do we have a clear incident response plan?
Sure.Currently, we encrypt all patient data both in transit and at rest. We use role-based access controls (RBAC) to ensure only authorized personnel can access certain data. We also conduct regular security audits and have real-time monitoring to detect unauthorized access attempts.
Role Based
Access
Control
XYZ Medical Center
It’s good to hear we’re prepared. Another area we need to address is our third-party vendors. How do we ensure they comply with our privacy and security standards?
All third-party vendors must sign a Business Associate Agreement (BAA), whichensures they comply with HIPAA standards. We also perform due diligence beforeengaging with them and conduct regular compliance audits.
Yes,we do. In case of a breach, our incident response plan involves immediate containment, assessing the scope of the breach, notifying affected patients, and reporting to regulatory authorities. We then conduct a root cause analysis and take steps to prevent future breaches.
Incident Response Plan
XYZ Medical Center
Great. The last point I would like to talk about is how we keep our staff updated on these practices. What’s our current approach, and how can we improve it?
We conduct regular training sessions and send out updates when there are changes in regulations or policies. However, we could improve by making these sessions more interactive and frequent, perhaps using scenarios and role-playing exercises to reinforce the material.
We can also implement stricter access controls for third-party vendors, ensuring they only access data necessary for their work. Regular reviews and audits of their security practices will help maintain compliance.
Access Denied - Stricter Policy
XYZ Medical Center
That sounds comprehensive. Thank you both for your insights. Let’s implement these improvements and continue to ensure we protect our patients’ data and maintain their trust.
Absolutely, Miranda. Regular reviews and improvements are key to staying ahead in privacy, consent, and security.
Agreed. We can also use an internal portal where staff can access up-to-date resources, complete mandatory training modules, and get immediate updates on any changes.
XYZ Internal Portal Employee
XYZ Medical Center
Good idea. Thanks again, both of you.
I’m on board.
I’m on board. Let’s schedule a follow-up meeting in a month to review our progress.
Schedule Meeting Open calendar
XYZ Medical Center
- Miranda: Director of the Patient Relations Department
- Yang: Compliance Officer
- Owen: IT Specialist
XYZ
IT Specialist
XYZ Medical Center
Hi Yang! Lets go and meet our Chief!
Hello Owen, yes, Miranda is waiting in the conference room.
XYZ Medical Center
Hi Owen, hi Yang. Thanks for making time to meet. I wanted to discuss our current practices around patient privacy, security, and consent, and see if there are areas we can improve.
Hi Miranda, thanks for organizing this. It’s always good to review these critical issues. Where should we begin?
Hi everyone. Maybe we can start with patient consent since it’s foundational to everything else. Miranda, what concerns do you have there?
XYZ Medical Center
I've noticed that some patients find our consent forms confusing and are unsure of what they agree to. How can we make this process more transparent for them?
We could simplify the language in our consent forms. Legal jargon can be intimidating, so plain language would help. Also, providing supplementary materials like a FAQ sheet or an informational video could clarify things for patients.
Adding to that, we could implement an electronic consent system that includes interactive elements. For example, pop-ups that explain each section in simple terms before the patient can proceed.
14:25
XYZ
Medical Center
XYZ Medical Center
Both ideas sound great. Simplifying the language and using interactive tools will make a big difference. What about security? Owen, can you go over our current measures and any gaps you’ve identified?
That’s a strong framework. But what if an unauthorized access attempt succeeds? Do we have a clear incident response plan?
Sure.Currently, we encrypt all patient data both in transit and at rest. We use role-based access controls (RBAC) to ensure only authorized personnel can access certain data. We also conduct regular security audits and have real-time monitoring to detect unauthorized access attempts.
Role Based
Access
Control
XYZ Medical Center
It’s good to hear we’re prepared. Another area we need to address is our third-party vendors. How do we ensure they comply with our privacy and security standards?
All third-party vendors must sign a Business Associate Agreement (BAA), whichensures they comply with HIPAA standards. We also perform due diligence beforeengaging with them and conduct regular compliance audits.
Yes,we do. In case of a breach, our incident response plan involves immediate containment, assessing the scope of the breach, notifying affected patients, and reporting to regulatory authorities. We then conduct a root cause analysis and take steps to prevent future breaches.
Incident Response Plan
XYZ Medical Center
Great. The last point I would like to talk about is how we keep our staff updated on these practices. What’s our current approach, and how can we improve it?
We conduct regular training sessions and send out updates when there are changes in regulations or policies. However, we could improve by making these sessions more interactive and frequent, perhaps using scenarios and role-playing exercises to reinforce the material.
We can also implement stricter access controls for third-party vendors, ensuring they only access data necessary for their work. Regular reviews and audits of their security practices will help maintain compliance.
Access Denied - Stricter Policy
XYZ Medical Center
That sounds comprehensive. Thank you both for your insights. Let’s implement these improvements and continue to ensure we protect our patients’ data and maintain their trust.
Absolutely, Miranda. Regular reviews and improvements are key to staying ahead in privacy, consent, and security.
Agreed. We can also use an internal portal where staff can access up-to-date resources, complete mandatory training modules, and get immediate updates on any changes.
XYZ Internal Portal Employee
XYZ Medical Center
Good idea. Thanks again, both of you.
I’m on board.
I’m on board. Let’s schedule a follow-up meeting in a month to review our progress.
Schedule Meeting Open calendar
XYZ Medical Center
- Miranda: Director of the Patient Relations Department
- Yang: Compliance Officer
- Owen: IT Specialist
XYZ
IT Specialist
XYZ Medical Center
Hi Yang! Lets go and meet our Chief!
Hello Owen, yes, Miranda is waiting in the conference room.
XYZ Medical Center
Hi Owen, hi Yang. Thanks for making time to meet. I wanted to discuss our current practices around patient privacy, security, and consent, and see if there are areas we can improve.
Hi Miranda, thanks for organizing this. It’s always good to review these critical issues. Where should we begin?
Hi everyone. Maybe we can start with patient consent since it’s foundational to everything else. Miranda, what concerns do you have there?
XYZ Medical Center
I've noticed that some patients find our consent forms confusing and are unsure of what they agree to. How can we make this process more transparent for them?
We could simplify the language in our consent forms. Legal jargon can be intimidating, so plain language would help. Also, providing supplementary materials like a FAQ sheet or an informational video could clarify things for patients.
Adding to that, we could implement an electronic consent system that includes interactive elements. For example, pop-ups that explain each section in simple terms before the patient can proceed.
14:25
XYZ
Medical Center
XYZ Medical Center
Both ideas sound great. Simplifying the language and using interactive tools will make a big difference. What about security? Owen, can you go over our current measures and any gaps you’ve identified?
That’s a strong framework. But what if an unauthorized access attempt succeeds? Do we have a clear incident response plan?
Sure.Currently, we encrypt all patient data both in transit and at rest. We use role-based access controls (RBAC) to ensure only authorized personnel can access certain data. We also conduct regular security audits and have real-time monitoring to detect unauthorized access attempts.
Role Based
Access
Control
XYZ Medical Center
It’s good to hear we’re prepared. Another area we need to address is our third-party vendors. How do we ensure they comply with our privacy and security standards?
All third-party vendors must sign a Business Associate Agreement (BAA), whichensures they comply with HIPAA standards. We also perform due diligence beforeengaging with them and conduct regular compliance audits.
Yes,we do. In case of a breach, our incident response plan involves immediate containment, assessing the scope of the breach, notifying affected patients, and reporting to regulatory authorities. We then conduct a root cause analysis and take steps to prevent future breaches.
Incident Response Plan
XYZ Medical Center
Great. The last point I would like to talk about is how we keep our staff updated on these practices. What’s our current approach, and how can we improve it?
We conduct regular training sessions and send out updates when there are changes in regulations or policies. However, we could improve by making these sessions more interactive and frequent, perhaps using scenarios and role-playing exercises to reinforce the material.
We can also implement stricter access controls for third-party vendors, ensuring they only access data necessary for their work. Regular reviews and audits of their security practices will help maintain compliance.
Access Denied - Stricter Policy
XYZ Medical Center
That sounds comprehensive. Thank you both for your insights. Let’s implement these improvements and continue to ensure we protect our patients’ data and maintain their trust.
Absolutely, Miranda. Regular reviews and improvements are key to staying ahead in privacy, consent, and security.
Agreed. We can also use an internal portal where staff can access up-to-date resources, complete mandatory training modules, and get immediate updates on any changes.
XYZ Internal Portal Employee
XYZ Medical Center
Good idea. Thanks again, both of you.
I’m on board.
I’m on board. Let’s schedule a follow-up meeting in a month to review our progress.
Schedule Meeting Open calendar
XYZ Medical Center
- Miranda: Director of the Patient Relations Department
- Yang: Compliance Officer
- Owen: IT Specialist
XYZ
IT Specialist
XYZ Medical Center
Hi Yang! Lets go and meet our Chief!
Hello Owen, yes, Miranda is waiting in the conference room.
XYZ Medical Center
Hi Owen, hi Yang. Thanks for making time to meet. I wanted to discuss our current practices around patient privacy, security, and consent, and see if there are areas we can improve.
Hi Miranda, thanks for organizing this. It’s always good to review these critical issues. Where should we begin?
Hi everyone. Maybe we can start with patient consent since it’s foundational to everything else. Miranda, what concerns do you have there?
XYZ Medical Center
I've noticed that some patients find our consent forms confusing and are unsure of what they agree to. How can we make this process more transparent for them?
We could simplify the language in our consent forms. Legal jargon can be intimidating, so plain language would help. Also, providing supplementary materials like a FAQ sheet or an informational video could clarify things for patients.
Adding to that, we could implement an electronic consent system that includes interactive elements. For example, pop-ups that explain each section in simple terms before the patient can proceed.
14:25
XYZ
Medical Center
XYZ Medical Center
Both ideas sound great. Simplifying the language and using interactive tools will make a big difference. What about security? Owen, can you go over our current measures and any gaps you’ve identified?
That’s a strong framework. But what if an unauthorized access attempt succeeds? Do we have a clear incident response plan?
Sure.Currently, we encrypt all patient data both in transit and at rest. We use role-based access controls (RBAC) to ensure only authorized personnel can access certain data. We also conduct regular security audits and have real-time monitoring to detect unauthorized access attempts.
Role Based
Access
Control
XYZ Medical Center
It’s good to hear we’re prepared. Another area we need to address is our third-party vendors. How do we ensure they comply with our privacy and security standards?
All third-party vendors must sign a Business Associate Agreement (BAA), whichensures they comply with HIPAA standards. We also perform due diligence beforeengaging with them and conduct regular compliance audits.
Yes,we do. In case of a breach, our incident response plan involves immediate containment, assessing the scope of the breach, notifying affected patients, and reporting to regulatory authorities. We then conduct a root cause analysis and take steps to prevent future breaches.
Incident Response Plan
XYZ Medical Center
Great. The last point I would like to talk about is how we keep our staff updated on these practices. What’s our current approach, and how can we improve it?
We conduct regular training sessions and send out updates when there are changes in regulations or policies. However, we could improve by making these sessions more interactive and frequent, perhaps using scenarios and role-playing exercises to reinforce the material.
We can also implement stricter access controls for third-party vendors, ensuring they only access data necessary for their work. Regular reviews and audits of their security practices will help maintain compliance.
Access Denied - Stricter Policy
XYZ Medical Center
That sounds comprehensive. Thank you both for your insights. Let’s implement these improvements and continue to ensure we protect our patients’ data and maintain their trust.
Absolutely, Miranda. Regular reviews and improvements are key to staying ahead in privacy, consent, and security.
Agreed. We can also use an internal portal where staff can access up-to-date resources, complete mandatory training modules, and get immediate updates on any changes.
XYZ Internal Portal Employee
XYZ Medical Center
Good idea. Thanks again, both of you.
I’m on board.
I’m on board. Let’s schedule a follow-up meeting in a month to review our progress.
Schedule Meeting Open calendar
XYZ Medical Center
- Miranda: Director of the Patient Relations Department
- Yang: Compliance Officer
- Owen: IT Specialist
XYZ
IT Specialist
XYZ Medical Center
Hi Yang! Lets go and meet our Chief!
Hello Owen, yes, Miranda is waiting in the conference room.
XYZ Medical Center
Hi Owen, hi Yang. Thanks for making time to meet. I wanted to discuss our current practices around patient privacy, security, and consent, and see if there are areas we can improve.
Hi Miranda, thanks for organizing this. It’s always good to review these critical issues. Where should we begin?
Hi everyone. Maybe we can start with patient consent since it’s foundational to everything else. Miranda, what concerns do you have there?
XYZ Medical Center
I've noticed that some patients find our consent forms confusing and are unsure of what they agree to. How can we make this process more transparent for them?
We could simplify the language in our consent forms. Legal jargon can be intimidating, so plain language would help. Also, providing supplementary materials like a FAQ sheet or an informational video could clarify things for patients.
Adding to that, we could implement an electronic consent system that includes interactive elements. For example, pop-ups that explain each section in simple terms before the patient can proceed.
14:25
XYZ
Medical Center
XYZ Medical Center
Both ideas sound great. Simplifying the language and using interactive tools will make a big difference. What about security? Owen, can you go over our current measures and any gaps you’ve identified?
That’s a strong framework. But what if an unauthorized access attempt succeeds? Do we have a clear incident response plan?
Sure.Currently, we encrypt all patient data both in transit and at rest. We use role-based access controls (RBAC) to ensure only authorized personnel can access certain data. We also conduct regular security audits and have real-time monitoring to detect unauthorized access attempts.
Role Based
Access
Control
XYZ Medical Center
It’s good to hear we’re prepared. Another area we need to address is our third-party vendors. How do we ensure they comply with our privacy and security standards?
All third-party vendors must sign a Business Associate Agreement (BAA), whichensures they comply with HIPAA standards. We also perform due diligence beforeengaging with them and conduct regular compliance audits.
Yes,we do. In case of a breach, our incident response plan involves immediate containment, assessing the scope of the breach, notifying affected patients, and reporting to regulatory authorities. We then conduct a root cause analysis and take steps to prevent future breaches.
Incident Response Plan
XYZ Medical Center
Great. The last point I would like to talk about is how we keep our staff updated on these practices. What’s our current approach, and how can we improve it?
We conduct regular training sessions and send out updates when there are changes in regulations or policies. However, we could improve by making these sessions more interactive and frequent, perhaps using scenarios and role-playing exercises to reinforce the material.
We can also implement stricter access controls for third-party vendors, ensuring they only access data necessary for their work. Regular reviews and audits of their security practices will help maintain compliance.
Access Denied - Stricter Policy
XYZ Medical Center
That sounds comprehensive. Thank you both for your insights. Let’s implement these improvements and continue to ensure we protect our patients’ data and maintain their trust.
Absolutely, Miranda. Regular reviews and improvements are key to staying ahead in privacy, consent, and security.
Agreed. We can also use an internal portal where staff can access up-to-date resources, complete mandatory training modules, and get immediate updates on any changes.
XYZ Internal Portal Employee
XYZ Medical Center
Good idea. Thanks again, both of you.
I’m on board.
I’m on board. Let’s schedule a follow-up meeting in a month to review our progress.
Schedule Meeting Open calendar
XYZ Medical Center
- Miranda: Director of the Patient Relations Department
- Yang: Compliance Officer
- Owen: IT Specialist
XYZ
IT Specialist
XYZ Medical Center
Hi Yang! Lets go and meet our Chief!
Hello Owen, yes, Miranda is waiting in the conference room.
XYZ Medical Center
Hi Owen, hi Yang. Thanks for making time to meet. I wanted to discuss our current practices around patient privacy, security, and consent, and see if there are areas we can improve.
Hi Miranda, thanks for organizing this. It’s always good to review these critical issues. Where should we begin?
Hi everyone. Maybe we can start with patient consent since it’s foundational to everything else. Miranda, what concerns do you have there?
XYZ Medical Center
I've noticed that some patients find our consent forms confusing and are unsure of what they agree to. How can we make this process more transparent for them?
We could simplify the language in our consent forms. Legal jargon can be intimidating, so plain language would help. Also, providing supplementary materials like a FAQ sheet or an informational video could clarify things for patients.
Adding to that, we could implement an electronic consent system that includes interactive elements. For example, pop-ups that explain each section in simple terms before the patient can proceed.
14:25
XYZ
Medical Center
XYZ Medical Center
Both ideas sound great. Simplifying the language and using interactive tools will make a big difference. What about security? Owen, can you go over our current measures and any gaps you’ve identified?
That’s a strong framework. But what if an unauthorized access attempt succeeds? Do we have a clear incident response plan?
Sure.Currently, we encrypt all patient data both in transit and at rest. We use role-based access controls (RBAC) to ensure only authorized personnel can access certain data. We also conduct regular security audits and have real-time monitoring to detect unauthorized access attempts.
Role Based
Access
Control
XYZ Medical Center
It’s good to hear we’re prepared. Another area we need to address is our third-party vendors. How do we ensure they comply with our privacy and security standards?
All third-party vendors must sign a Business Associate Agreement (BAA), whichensures they comply with HIPAA standards. We also perform due diligence beforeengaging with them and conduct regular compliance audits.
Yes,we do. In case of a breach, our incident response plan involves immediate containment, assessing the scope of the breach, notifying affected patients, and reporting to regulatory authorities. We then conduct a root cause analysis and take steps to prevent future breaches.
Incident Response Plan
XYZ Medical Center
Great. The last point I would like to talk about is how we keep our staff updated on these practices. What’s our current approach, and how can we improve it?
We conduct regular training sessions and send out updates when there are changes in regulations or policies. However, we could improve by making these sessions more interactive and frequent, perhaps using scenarios and role-playing exercises to reinforce the material.
We can also implement stricter access controls for third-party vendors, ensuring they only access data necessary for their work. Regular reviews and audits of their security practices will help maintain compliance.
Access Denied - Stricter Policy
XYZ Medical Center
That sounds comprehensive. Thank you both for your insights. Let’s implement these improvements and continue to ensure we protect our patients’ data and maintain their trust.
Absolutely, Miranda. Regular reviews and improvements are key to staying ahead in privacy, consent, and security.
Agreed. We can also use an internal portal where staff can access up-to-date resources, complete mandatory training modules, and get immediate updates on any changes.
XYZ Internal Portal Employee
XYZ Medical Center
Good idea. Thanks again, both of you.
I’m on board.
I’m on board. Let’s schedule a follow-up meeting in a month to review our progress.
Schedule Meeting Open calendar
XYZ Medical Center
- Miranda: Director of the Patient Relations Department
- Yang: Compliance Officer
- Owen: IT Specialist
XYZ
IT Specialist
XYZ Medical Center
Hi Yang! Lets go and meet our Chief!
Hello Owen, yes, Miranda is waiting in the conference room.
XYZ Medical Center
Hi Owen, hi Yang. Thanks for making time to meet. I wanted to discuss our current practices around patient privacy, security, and consent, and see if there are areas we can improve.
Hi Miranda, thanks for organizing this. It’s always good to review these critical issues. Where should we begin?
Hi everyone. Maybe we can start with patient consent since it’s foundational to everything else. Miranda, what concerns do you have there?
XYZ Medical Center
I've noticed that some patients find our consent forms confusing and are unsure of what they agree to. How can we make this process more transparent for them?
We could simplify the language in our consent forms. Legal jargon can be intimidating, so plain language would help. Also, providing supplementary materials like a FAQ sheet or an informational video could clarify things for patients.
Adding to that, we could implement an electronic consent system that includes interactive elements. For example, pop-ups that explain each section in simple terms before the patient can proceed.
14:25
XYZ
Medical Center
XYZ Medical Center
Both ideas sound great. Simplifying the language and using interactive tools will make a big difference. What about security? Owen, can you go over our current measures and any gaps you’ve identified?
That’s a strong framework. But what if an unauthorized access attempt succeeds? Do we have a clear incident response plan?
Sure.Currently, we encrypt all patient data both in transit and at rest. We use role-based access controls (RBAC) to ensure only authorized personnel can access certain data. We also conduct regular security audits and have real-time monitoring to detect unauthorized access attempts.
Role Based
Access
Control
XYZ Medical Center
It’s good to hear we’re prepared. Another area we need to address is our third-party vendors. How do we ensure they comply with our privacy and security standards?
All third-party vendors must sign a Business Associate Agreement (BAA), whichensures they comply with HIPAA standards. We also perform due diligence beforeengaging with them and conduct regular compliance audits.
Yes,we do. In case of a breach, our incident response plan involves immediate containment, assessing the scope of the breach, notifying affected patients, and reporting to regulatory authorities. We then conduct a root cause analysis and take steps to prevent future breaches.
Incident Response Plan
XYZ Medical Center
Great. The last point I would like to talk about is how we keep our staff updated on these practices. What’s our current approach, and how can we improve it?
We conduct regular training sessions and send out updates when there are changes in regulations or policies. However, we could improve by making these sessions more interactive and frequent, perhaps using scenarios and role-playing exercises to reinforce the material.
We can also implement stricter access controls for third-party vendors, ensuring they only access data necessary for their work. Regular reviews and audits of their security practices will help maintain compliance.
Access Denied - Stricter Policy
XYZ Medical Center
That sounds comprehensive. Thank you both for your insights. Let’s implement these improvements and continue to ensure we protect our patients’ data and maintain their trust.
Absolutely, Miranda. Regular reviews and improvements are key to staying ahead in privacy, consent, and security.
Agreed. We can also use an internal portal where staff can access up-to-date resources, complete mandatory training modules, and get immediate updates on any changes.
XYZ Internal Portal Employee
XYZ Medical Center
Good idea. Thanks again, both of you.
I’m on board.
I’m on board. Let’s schedule a follow-up meeting in a month to review our progress.
Schedule Meeting Open calendar
XYZ Medical Center
- Miranda: Director of the Patient Relations Department
- Yang: Compliance Officer
- Owen: IT Specialist
XYZ
IT Specialist
XYZ Medical Center
Hi Yang! Lets go and meet our Chief!
Hello Owen, yes, Miranda is waiting in the conference room.
XYZ Medical Center
Hi Owen, hi Yang. Thanks for making time to meet. I wanted to discuss our current practices around patient privacy, security, and consent, and see if there are areas we can improve.
Hi Miranda, thanks for organizing this. It’s always good to review these critical issues. Where should we begin?
Hi everyone. Maybe we can start with patient consent since it’s foundational to everything else. Miranda, what concerns do you have there?
XYZ Medical Center
I've noticed that some patients find our consent forms confusing and are unsure of what they agree to. How can we make this process more transparent for them?
We could simplify the language in our consent forms. Legal jargon can be intimidating, so plain language would help. Also, providing supplementary materials like a FAQ sheet or an informational video could clarify things for patients.
Adding to that, we could implement an electronic consent system that includes interactive elements. For example, pop-ups that explain each section in simple terms before the patient can proceed.
14:25
XYZ
Medical Center
XYZ Medical Center
Both ideas sound great. Simplifying the language and using interactive tools will make a big difference. What about security? Owen, can you go over our current measures and any gaps you’ve identified?
That’s a strong framework. But what if an unauthorized access attempt succeeds? Do we have a clear incident response plan?
Sure.Currently, we encrypt all patient data both in transit and at rest. We use role-based access controls (RBAC) to ensure only authorized personnel can access certain data. We also conduct regular security audits and have real-time monitoring to detect unauthorized access attempts.
Role Based
Access
Control
XYZ Medical Center
It’s good to hear we’re prepared. Another area we need to address is our third-party vendors. How do we ensure they comply with our privacy and security standards?
All third-party vendors must sign a Business Associate Agreement (BAA), whichensures they comply with HIPAA standards. We also perform due diligence beforeengaging with them and conduct regular compliance audits.
Yes,we do. In case of a breach, our incident response plan involves immediate containment, assessing the scope of the breach, notifying affected patients, and reporting to regulatory authorities. We then conduct a root cause analysis and take steps to prevent future breaches.
Incident Response Plan
XYZ Medical Center
Great. The last point I would like to talk about is how we keep our staff updated on these practices. What’s our current approach, and how can we improve it?
We conduct regular training sessions and send out updates when there are changes in regulations or policies. However, we could improve by making these sessions more interactive and frequent, perhaps using scenarios and role-playing exercises to reinforce the material.
We can also implement stricter access controls for third-party vendors, ensuring they only access data necessary for their work. Regular reviews and audits of their security practices will help maintain compliance.
Access Denied - Stricter Policy
XYZ Medical Center
That sounds comprehensive. Thank you both for your insights. Let’s implement these improvements and continue to ensure we protect our patients’ data and maintain their trust.
Absolutely, Miranda. Regular reviews and improvements are key to staying ahead in privacy, consent, and security.
Agreed. We can also use an internal portal where staff can access up-to-date resources, complete mandatory training modules, and get immediate updates on any changes.
XYZ Internal Portal Employee
XYZ Medical Center
Good idea. Thanks again, both of you.
I’m on board.
I’m on board. Let’s schedule a follow-up meeting in a month to review our progress.
Schedule Meeting Open calendar
XYZ Medical Center
- Miranda: Director of the Patient Relations Department
- Yang: Compliance Officer
- Owen: IT Specialist
XYZ
IT Specialist
Storyboard Text
- Slide: 1
- Hi Yang! Lets go and meet our Chief!
- XYZ Medical Center
- Hello Owen, yes, Miranda is waiting in the conference room.
- 14:25
- Slide: 2
- Hi Owen, hi Yang. Thanks for making time to meet. I wanted to discuss our current practices around patient privacy, security, and consent, and see if there are areas we can improve.
- Hi Miranda, thanks for organizing this. It’s always good to review these critical issues. Where should we begin?
- XYZ Medical Center
- Hi everyone. Maybe we can start with patient consent since it’s foundational to everything else. Miranda, what concerns do you have there?
- Slide: 3
- I've noticed that some patients find our consent forms confusing and are unsure of what they agree to. How can we make this process more transparent for them?
- We could simplify the language in our consent forms. Legal jargon can be intimidating, so plain language would help. Also, providing supplementary materials like a FAQ sheet or an informational video could clarify things for patients.
- XYZ Medical Center
- XYZMedical Center
- Adding to that, we could implement an electronic consent system that includes interactive elements. For example, pop-ups that explain each section in simple terms before the patient can proceed.
- Slide: 4
- That’s a strong framework. But what if an unauthorized access attempt succeeds? Do we have a clear incident response plan?
- Both ideas sound great. Simplifying the language and using interactive tools will make a big difference. What about security? Owen, can you go over our current measures and any gaps you’ve identified?
- XYZ Medical Center
- Role BasedAccessControl
- Sure.Currently, we encrypt all patient data both in transit and at rest. We use role-based access controls (RBAC) to ensure only authorized personnel can access certain data. We also conduct regular security audits and have real-time monitoring to detect unauthorized access attempts.
- Slide: 5
- All third-party vendors must sign a Business Associate Agreement (BAA), whichensures they comply with HIPAA standards. We also perform due diligence beforeengaging with them and conduct regular compliance audits.
- It’s good to hear we’re prepared. Another area we need to address is our third-party vendors. How do we ensure they comply with our privacy and security standards?
- XYZ Medical Center
- Incident Response Plan
- Yes,we do. In case of a breach, our incident response plan involves immediate containment, assessing the scope of the breach, notifying affected patients, and reporting to regulatory authorities. We then conduct a root cause analysis and take steps to prevent future breaches.
- Slide: 6
- We conduct regular training sessions and send out updates when there are changes in regulations or policies. However, we could improve by making these sessions more interactive and frequent, perhaps using scenarios and role-playing exercises to reinforce the material.
- Great. The last point I would like to talk about is how we keep our staff updated on these practices. What’s our current approach, and how can we improve it?
- XYZ Medical Center
- Access Denied - Stricter Policy
- We can also implement stricter access controls for third-party vendors, ensuring they only access data necessary for their work. Regular reviews and audits of their security practices will help maintain compliance.
- Slide: 7
- That sounds comprehensive. Thank you both for your insights. Let’s implement these improvements and continue to ensure we protect our patients’ data and maintain their trust.
- Absolutely, Miranda. Regular reviews and improvements are key to staying ahead in privacy, consent, and security.
- XYZ Medical Center
- XYZ Internal Portal Employee
- Agreed. We can also use an internal portal where staff can access up-to-date resources, complete mandatory training modules, and get immediate updates on any changes.
- Slide: 8
- I’m on board.
- XYZ Medical Center
- Good idea. Thanks again, both of you.
- Schedule Meeting Open calendar
- I’m on board. Let’s schedule a follow-up meeting in a month to review our progress.
- Slide: 9
- XYZ Medical Center
- XYZIT Specialist
- Owen: IT Specialist
- Miranda: Director of the Patient Relations Department
- Yang: Compliance Officer


